Winning the attack: Four steps to protecting your practice against cyberattacks
Ransomware: Software that holds data “hostage” until a ransom is paid.
Phishing: The fraudulent practice of sending emails purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers.
According to Cybercrime Magazine, ransomware is the fastest growing type of cyberattack in the US.1 The US Department of Justice has called ransomware the “new business model for cybercrime.”2 In fact, the damage caused by ransomware is predicted to cost the world $20 billion in 2021.3
Unfortunately, dentistry, with its sensitive patient and practice data, is attractive to cybercriminals. ForgeRock’s Consumer Identity Breach Report for 2021 states that attacks against the health-care industry accounted for 34% of breaches in 2020. While this accounted for only 1% of all record thefts, the cost of mitigation was $474/record—which is three times the cost of other industries.
Cyberattacks can happen in any number of ways. According to Security magazine, there are more than 2,200 attacks each day, which breaks down to nearly one cyberattack every 39 seconds. The most common way an intruder can gain access to your key systems is through compromised accounts—meaning someone has accessed your system by stealing or guessing passwords, often through phishing scams. In the past year there has been an estimated 450% increase in these types of intrusions.
Read related content:
5 tips to help dentists boost their cybersecurity
How dentists can protect themselves from the cyberattack epidemic
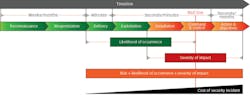
Practices must realize it is not a matter of if an attack is going to happen, but rather when. In most cybersecurity attacks, the enemies are external cybercriminals who tend to follow a similar pattern when they attack. Also known as the “cyber kill chain,” a concept first introduced by Lockheed Martin, this model outlines the common steps a cybercriminal takes to achieve their goal of breaching a system. The ultimate goal of the attacker is accessing and stealing your data. Sometimes the data is then sold on the dark web or held ransom until you pay an exorbitant fee to regain access.
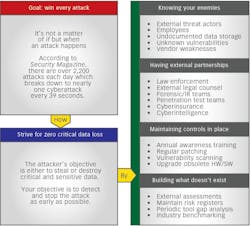
As such, the goal of your practice’s security strategy is to win the attack by striving for zero critical data loss. This is accomplished by stopping the intruder early in the kill chain when a cyber intrusion occurs. The diagram below developed by Klaus Jochem in his article “IT Security Matters” demonstrates how by disrupting the kill chain early, you lower the impact severity of the event and the costs associated with mitigations.
You can win the battle by following these four key steps.
Step 1: Know your enemies, know yourself—identify weaknesses before they do
Sun Tzu in The Art of War states that “if you know the enemy and know yourself, you need not fear the result of a hundred battles. If you know yourself but not the enemy, for every victory gained you will also suffer a defeat. If you know neither the enemy nor yourself, you will succumb in every battle.”
To be successful in thwarting a cybersecurity attack, you need to “know the enemy” and “know yourself.”
First, let’s focus on knowing the enemy. The first stage of the kill chain is reconnaissance, where the intruder learns all that they can about your practice, its leaders, its routines, its partners and any known vulnerabilities they can identify by probing your Internet-facing systems: your practice website and social media. In this phase, the enemy is learning everything they can about your practice’s weaknesses.
This is why you also need to know yourself. If you don’t understand your weaknesses, how can you stop an intruder from exploiting them? The key steps to building a more robust security posture are:
- Having a clear understanding of where your critical data—whether it’s patient or practice data—is being processed and stored, and who has access to that information. By doing this, you document your critical “processing activities,” such as your dental practice management software, and accounting and payroll systems where sensitive data is managed. Mapping these processing activities helps you understand what the enemy’s potential targets are within your business. This process is also a HIPAA and GDPR requirement.
- Understanding all the vendors involved in supporting your processing activities that support your computer systems, applications, and network communications. Evaluate any risks they may have to compromise your data through periodic assessments and verification of certifications. Third-party vendor evaluation tools are available from vendors such as OneTrust or services such as CORL Technologies.
- Periodically checking your IT environment for vulnerabilities using internal scanning tools, external scanning services (e.g., SecurityScorecard or BitSight) and having annual penetration tests conducted by professional services. This would include your DPMS and other applications; the computer systems they run on; and your practice’s computer network.
Another key aspect of this step is trusting that your employees follow good security practices; know how to spot an intrusion; and know what to do if one happens. You accomplish this by providing them with robust annual security awareness on good password management; recognizing phishing emails and how to report them; and how to protect their identities on social media and not share information potential intruders could use or exploit in phishing campaigns. You should also periodically perform email phishing tests to test your employees’ knowledge. There are several vendors in this space that can provide these services to your organization.
Step 2: Build strong external partnerships—relying on allies
Like any good general, you’ll need to call on your allies from time to time to fill in gaps you may not have knowledge of when fighting against cybercriminals. Your practice should maintain strong external partnerships to win the attack.
To help you know your enemy, these partnerships include:
- Law enforcement agencies and knowing who to contact in case of an intrusion. For instance, cybercrime is usually reported to the FBI, while any HIPAA violations are overseen by Health and Human Services.
- Forensic and incident response vendors to assist your recovery efforts and aid you in determining how an attack occurred so that you can fix any issues
- Outside legal counsel to assist with any customer or government reporting
- Cyber insurance companies who can assist your business in transferring the costs associated with recovery from a cyber-related event
- Cyber intelligence organizations that can continually monitor the dark web to identify potential threat actors who might be watching your organization, or who have obtained information that is being sold on the dark web about your organization (i.e., compromised passwords and vulnerable systems)
To help you know yourself, these partnerships should include:
- Penetration testing organizations to periodically test your environment for vulnerabilities
- Security tool vendors who assist in identifying and remediating vulnerabilities in your environment
- Partners running secure hosted platform environments to support your business operations. This allows you to transfer/outsource a significant amount of your security overhead to secure service providers, such as Carestream Dental.
Step 3: Maintain controls in place—the best defense is a good offense
These steps outline the process most cybercriminals take to gain access to your data and the actions you should consider having in place to disrupt the kill chain:
- Reconnaissance: The enemy begins researching your practice, so you watch your social media presence and use different passwords to avoid being a target. You can visit haveIbeenpwned.com to see what kind of practice information may be floating around on the internet that you’re not aware of.
- Weaponization: This is when the enemy prepares to access your accounts, whether through a phishing scheme or by guessing passwords for access; there really are no actions you can take here.
- Delivery: Your enemy deploys their “weapon”—this could be a link in fake email or even a USB drive. You can be prepared by enabling antivirus tools, filtering your emails and web access, educating your team, conducting phishing exercises, limiting outside USB devices, and blocking auto-run on devices.
- Exploitation: Assuming the weapon gains access to your system, this is when staying up to date on security patches, scanning for vulnerabilities, and protecting your website with web applications with firewalls will pay off.
- Installation: This is when the malware is installed on your system, allowing the enemy to gain access, but anti-virus tools, controlling who has admin rights to your systems, multifactor controls, and whitelist tools for software helps mitigate the risk of this happening.
- Command and control: If this does happen, the enemy can remotely control your systems. However, implementing firewalls, enabling intrusion protection systems, and utilizing proxy filters can stop them from getting this far.
- Actions on objectives: Unfortunately, if the enemy gets this far, it’s time to call in your allies. Make sure your backup files are secure, put your disaster recovery plan into action, contact your cyber insurance provider and consider a forensic IR retainer.
Having these key controls in place will minimize the risk, severity, and cost associated with an event, and will help you achieve your audit and compliance needs.
Step 4: Build what doesn’t exist—filling in the gaps
Security is not a “one and done” initiative. It is an ongoing cycle of continuous improvement that requires constant reassessment based on ever-changing threats and vulnerabilities.
For example, Carestream Dental’s Information Security Program is based on sound risk management principles and a lifecycle of continuous improvement as depicted in the Carestream Dental Security Program Lifecycle.
Based on your reviews, you should consider taking the appropriate steps to put them into place as quickly as possible. These include filling any gaps in external relationships, building knowledge about your processing activities, or installing missing security tools to defend against attacks.
Don’t let the potential for a cybersecurity breach keep you from evolving with the digital world. If managing these resources internally within your environment seems daunting, consider moving sensitive data management into trusted secure cloud-service providers, such as Carestream Dental’s Sensei Cloud. Moving to the cloud can be intimidating, but with the right security platforms in place, you can feel confident about the digital environment for your practice.
References
1. Morgan S. Global cybercrime damages predicted to reach $6 trillion annually by 2021. Cybercrime Magazine. December 7, 2018. Accessed August 30, 2021. https://cybersecurityventures.com/cybercrime-damages-6-trillion-by-2021/
2. Rosenstein R. Cambridge Cyber Summit. Edward M. Kennedy Institute, Boston, Mass. October 4, 2017. Cyber Crime and Punishment.
3.Morgan S. Global ransomware damage costs predicted to hit $20 billion (USD) by 2021. Cybercrime Magazine. October 21, 2019. Accessed August 30, 2021. https://cybersecurityventures.com/global-ransomware-damage-costs-predicted-to-reach-20-billion-usd-by-2021/
John Bruggemann is Carestream Dental’s Global Information Security Officer (GISO) and is located in Atlanta, Georgia. He is responsible for information security and partners with the Legal, Compliance, and Product Development teams to drive Carestream Dental’s cybersecurity compliance efforts for GDPR, HIPAA, and PCI.
About the Author
John Bruggemann
John Bruggemann is Carestream Dental’s Global Information Security Officer (GISO) and is located in Atlanta, Georgia. He is responsible for information security and partners with the Legal, Compliance, and Product Development teams to drive Carestream Dental’s cybersecurity compliance efforts for GDPR, HIPAA, and PCI.